Orphaned Workspaces
Syskit Point detects workspaces that don't have active owners, which helps ensure that there is always someone responsible for access and content management in your workspaces.
When the task delegation option is enabled for the Orphaned Workspaces policy, Syskit Point creates tasks and sends e-mails to users as defined in the policy settings. To learn more, take a look at the Orphaned Workspaces policy article.
By default, task delegation is turned off for this policy, but the orphaned workspaces are still detected and visible on the Security and Compliance dashboard. This means that Syskit Point detects a vulnerability in a workspace based on the applied policy, but it does not create tasks or send any e-mails to workspace owners.
The purpose of this is to assist Syskit Point admins by bringing awareness of potential issues in their Microsoft 365 environment.
On the Security & Compliance dashboard, click the Orphaned Workspaces button to access the report.
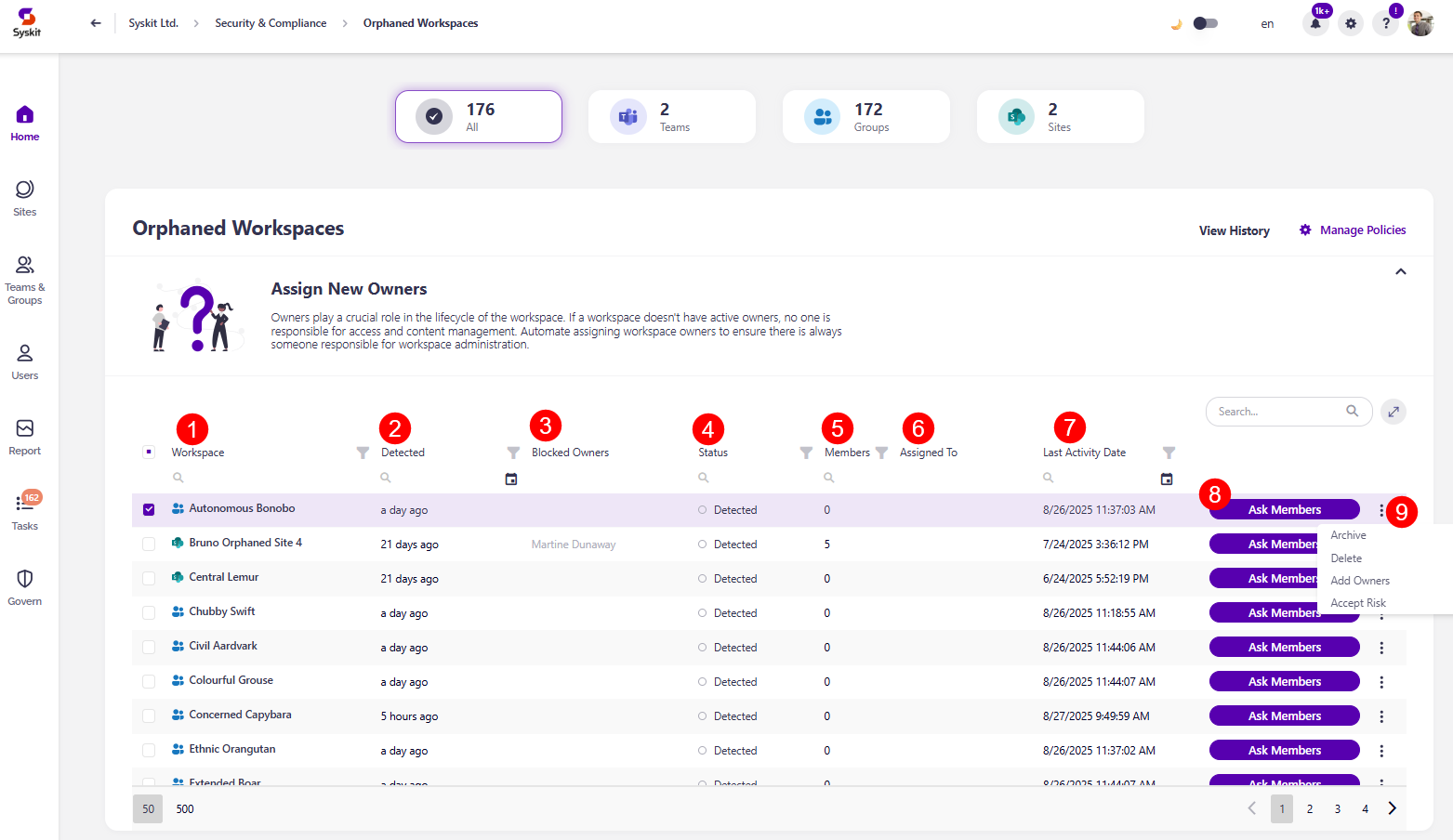
The Orphaned Workspaces screen opens, showing a list of all workspaces that don't have active owners.
Above the report, you can see the workspace type filters along with the number of workspaces where the vulnerability was detected:
- All workspaces
- Microsoft Teams
- Microsoft Groups
- SharePoint Sites Click the filter to show the specific workspace type in the report.
The report itself provides information on:
- Workspace (1) name
- Detected (2) - when the policy vulnerability was detected
- Blocked Owners (3) - the names of workspace owners that have been blocked
- Status (4) - status of the policy vulnerability
- If a vulnerability was detected, the status shows as Detected
- If task delegation is enabled for the policy, it shows the task status, for example, Awaiting response from members
- Members (5) - the number of members in the workspace
- Assigned to (6) - to whom the policy vulnerability tasks are assigned for resolution
- Last Activity Date (7) - the date and time when activity was last logged on the workspace
Additionally, you can complete the following actions for the policy vulnerability:
- Ask Members (8) - this action will send e-mails and create tasks for the workspace members to suggest new workspace owners; available only on workspaces where task delegation is not enabled
- If task delegation is enabled in the policy settings, the Send Reminder action is available instead of the Ask Members action
- For more details on the Ask Members action, please check out the section below
- The Ellipsis (more options) Menu (9) - clicking the 3 dots next to the visible action buttons provides the option to complete the following actions:
- Archive - this action archives the workspace
- Delete - this action deletes the workspace
- Add Owners - this action lets you manually add additional owners to the workspace to resolve the task yourself
- Accept Risk - this action means you will close the policy vulnerability task without making any changes to the current state of the workspace
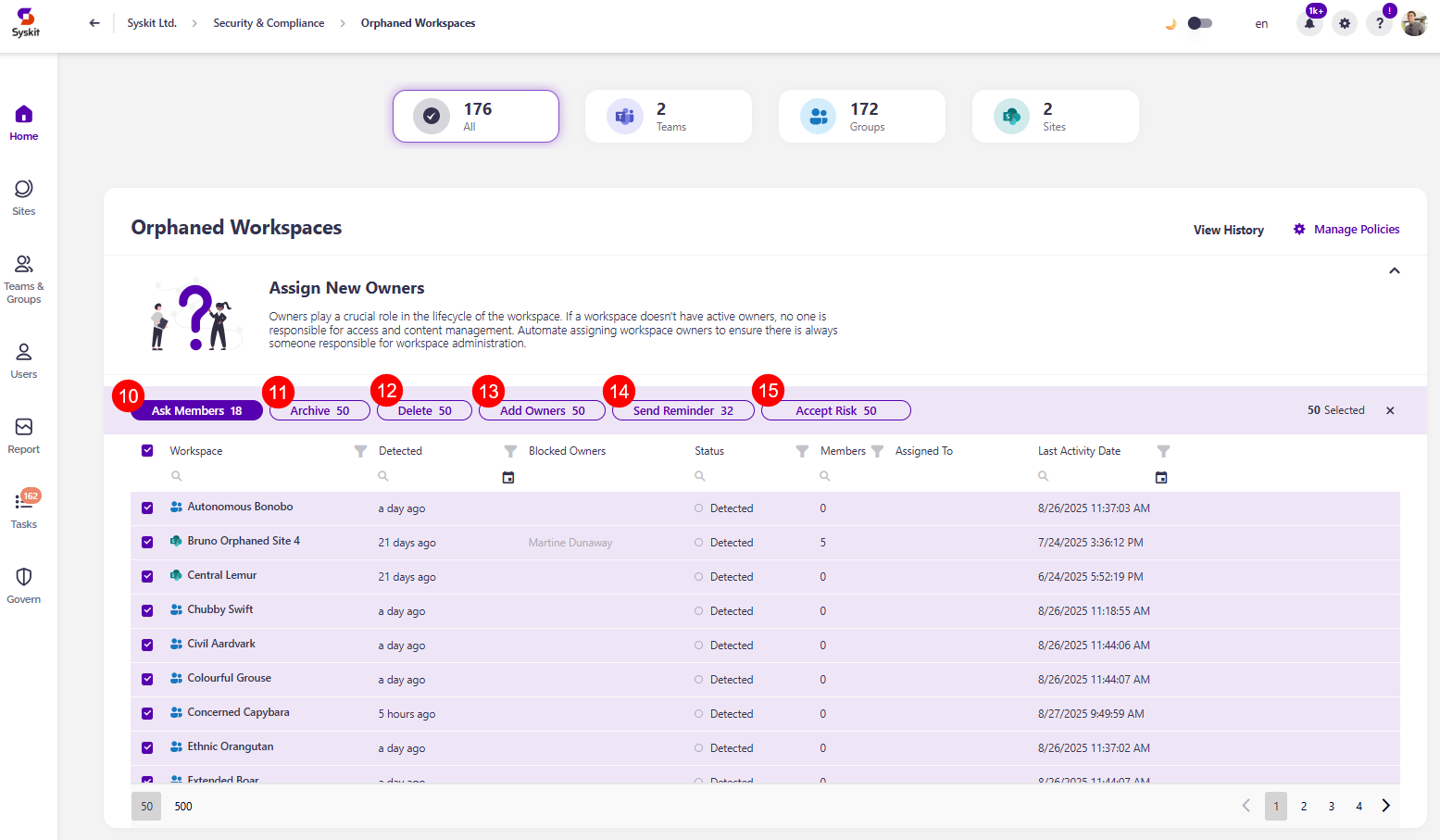
By selecting all (10) or more than one workspace, you can perform the bulk action for Archive (11), Delete (12), Add Owners (13), Send reminder (14), and Accept risk (15).
To find more details for a specific workspace, click the workspace name on the report.
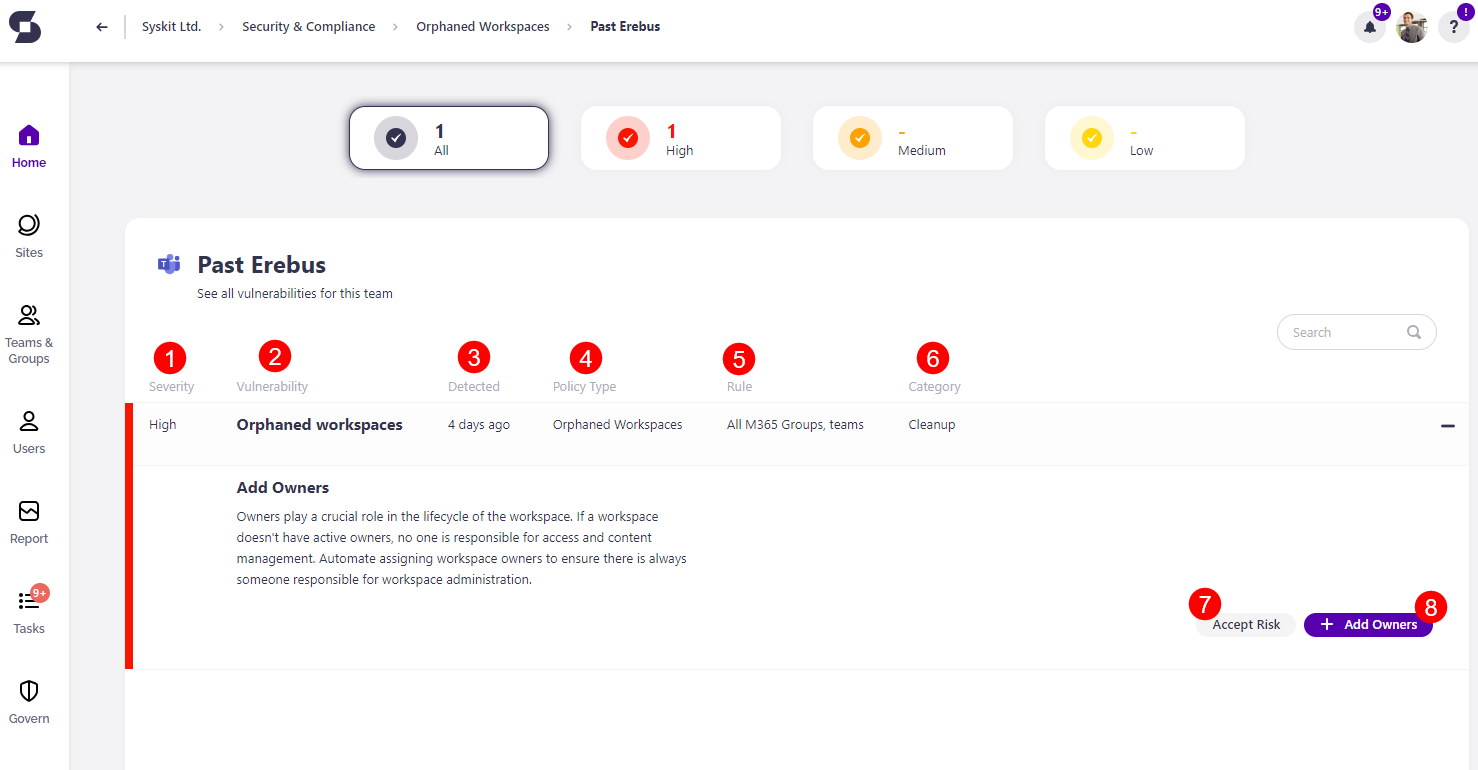
- This opens the screen that shows more details about the workspace
Here you can find the following information:
- Severity level (1)
- Vulnerability (2)
- Detected (3)
- Policy Type (4)
- Rule (5)
- Category (6)
You can also perform the actions to Accept Risk (7) and Add Owners (8).
Additional information:
- Nested group members are counted when resolving a policy.
- If the required number of members has not been added or removed, including those within nested groups, the Resolve button remains disabled until that condition is met.
- For SharePoint sites, site Owners are determined by the SharePoint Owners group.
- Only users who are part of the SharePoint Owners group are considered Site Owners and can resolve tasks. Site Admins cannot resolve tasks and are not considered Site Owners.
Ask Members Action
The Ask Members action helps resolve orphaned workspace tasks by asking workspace members to suggest new owners when no active owners exist.
The Ask Members action is a two-stage process:
- Stage One - Members suggest new owners
- When the Ask Members action is triggered, e-mails and tasks are sent to all members of the workspace
- Members are asked to suggest one or more users as new owners
- Members can resolve the task directly from the e-mail they receive
- The suggestions are stored as members resolve their tasks, and stage one stays active until all members resolve their tasks
Please note:
If the team has no members, this action cannot be completed. In that case, the admins have to resolve the vulnerability by using one of the following actions;
- Add Owners
- Archive Workspace
- Delete Workspace
- Stage 2 - Resolving the task
- After all members complete their tasks, a new task is created for admins or designated reviewers to take one of the following actions:
- Add Owners, by approving the suggestions made by members or deciding on an owner yourself
- Archive the workspace
- Delete the workspace
- After all members complete their tasks, a new task is created for admins or designated reviewers to take one of the following actions:
For more details on how the Ask Members task resolution looks from the perspective of members who receive the task, take a look at the Resolve Orphaned Workspaces Tasks.
The policy vulnerability is closed only after the second stage is resolved. Collecting suggestions alone from members does not close the vulnerability.
Tasks are sent to all workspace members. If a Guest User is a member, they will receive the task as well and can submit suggestions.
Users have 15 days to resolve Tasks. After 15 days, the second stage is triggered, and the approval task is created.
Users cannot become owners based on suggestions alone; Point Admin or a specified custom recipient must approve this decision during stage 2.
Designated Reviewers
Designated reviewers for Stage 2 are determined using the following rules:
- Point tries to use the currently defined reviewers and respects existing policy settings
- If specific reviewers are selected as custom recipients in the policy settings, the task is sent to them
- If the reviewer type is set to custom recipients, but the defined users cannot be found, the task is sent to Point Admins